For the first time in just over a year there has been a new release of the Subsonic media server.
An updated snap package is available from the Snap Store, or by clicking on the button on the right.
Wednesday, November 14, 2018
Monday, October 15, 2018
Printing documents from Ubuntu Touch
Early previews of Ubuntu Touch 16.04 OTA-4 came with a settings panel for configuring printers. But the dual concerns of a root image that was growing too large, and the unfinished feature being deemed expendable conspired to make it so that the feature was dropped in subsequent previews. It has not made a reappearance in the recently released OTA-5 either. I expect it will be revisited when space is made available in the root image by removing some deprecated libraries.
I got to thinking that it should be possible to set up printing in a Libertine container. And turns out it is! Let's walk through the steps. I will assume that you already have a running Libertine container. Lets call ours xenial. I will also assume that you have a network printer that is accessible in a browser under http://<address of printer server>:631. In other words, that you have a CUPS server running somewhere on your local network. For the purposes of this walk-through let us assume the IP address of the server is 192.168.0.4
Next enter the container shell:
Notice that if you have more than one container on your device and you want to be able to print from within that container also, you would have to repeat the above steps for that container also. So it might be worth it to take a moment to consider how you want to distribute your applications among the different containers.
Need To Print
But what if I want to be able to print the attachment of an email from the convenience of my mobile device? Going up the stairs, turning on the desktop, waiting for it to boot, logging in, opening my email, then printing the attachment, takes up so much time! Accessing the correct email is so much faster on my phone. So I would want to be able to print from it too.I got to thinking that it should be possible to set up printing in a Libertine container. And turns out it is! Let's walk through the steps. I will assume that you already have a running Libertine container. Lets call ours xenial. I will also assume that you have a network printer that is accessible in a browser under http://<address of printer server>:631. In other words, that you have a CUPS server running somewhere on your local network. For the purposes of this walk-through let us assume the IP address of the server is 192.168.0.4
The Setup
Fire up the Terminal app in Ubuntu Touch and install the CUPS client package in the xenial container:$ libertine-container-manager install-package -i xenial -p cups-clientWe only want the client package since we will not be running a CUPS server locally in the container. This would not have been possible even if we wanted to, because daemons cannot be started inside Libertine containers.
Next enter the container shell:
$ libertine-container-manager exec -i xenial -c /bin/bashYou will now be in a root shell inside the xenial container. What we need to do here is tell the CUPS client where to look for a CUPS server. The default location is localhost. But we wouldn't be running a CUPS server on the device itself. So we need to point it to our server. Remember that ours is running at address 192.168.0.4:
# mkdir -p /etc/cups # touch /etc/cups/client.conf # echo "ServerName 192.168.0.4" >> /etc/cups/client.confNow you should be able to print from any other application installed in the container. Just install your favorite editor and viewers alongside. In my setup I have installed firefox, libreoffice and evince.
Notice that if you have more than one container on your device and you want to be able to print from within that container also, you would have to repeat the above steps for that container also. So it might be worth it to take a moment to consider how you want to distribute your applications among the different containers.
Saturday, October 13, 2018
Migrating from ElementaryOS 0.4 to Ubuntu 16.04 without reinstalling
The Good
ElementaryOS is one handsome Linux distribution. It is elegant in the execution and I would recommend it to any Apple refugees who're not tied to any exclusively MacOS applications, along with any newcomer to Linux in general.It had been my distribution of choice on a netbook at home for a while to my great satisfaction. So when it came time to replace my development workstation I thought, "Why not give Elementary a go in the work environment?"
The Bad
The Elementary team deservedly pride themselves in delivering a coherent experience. The project has its own UI and UX guidelines, its own toolkit, its own libraries, its own utilities and applications like the desktop and terminal app to name just two. This is understandable, because it helps give the user a consistent interface and experience.But the applications I use in my work environment make assumptions about the environment they are running on, and try to integrate with that environment. For example: at my job we use Subversion as our revision control solution. We also use C# as the main development language. So RabbitVCS and MonoDevelop are an important part of my everyday workflow. But RabbitVCS integrates with Gnome's Files (nautilus) but not with Elementary's Files (pantheon-files). Similarly MonoDevelop fails to launch a console application for debugging if Gnome's Terminal application (gnome-terminal) is not installed, thereby completely ignoring the availability of Elementary's Terminal application (pantheon-terminal).
I also needed to run DBeaver, Thunderbird and Virtual Machine Manager, to name a few of the other applications that are outside of the Elementary ecosystem. Granted, it is easy enough to install these applications. But having them living on my desktop destroyed the aesthetic harmony that was the main reason to run this distribution in the first place.
So after some internal deliberation I decided that I might just as well migrate my machine to Ubuntu, as that would be more in line to what the applications I use expect to be running on.
And The Ugly
Being that Elementary is based on Ubuntu I wanted to perform the migration without requiring a reinstall. But what packages would I need to install and uninstall to leave my machine running as if I had installed Ubuntu on it in the first place?I decided to fire up a VM on my laptop to investigate. I first installed ElementaryOS 0.4.1 Loki (the current stable, and the one I run on my workstation) on it. Then I went about installing the ubuntu-desktop meta packages, which pulled in and installed all the dependencies:
$ sudo apt install sudo apt install ubuntu-desktopNext I removed every package that I could find that was obviously related to ElementaryOS and the pantheon distribution:
$ sudo apt --purge autoremove elementary-desktop elementary-standard \ elementary-minimal plymouth-theme-elementary* \ elementary-icon-theme elementary-theme libgranite-common \ pantheon-terminal libwingpanel-2.0-0 elementary-dpms-helper \ libreoffice-style-elementary libswitchboard-2.0-0Lastly I disabled the ElementaryOS specific repositories under Software-Updates:
After a reboot, I had me an Ubuntu 16.04 with Unity 7 that looked like it was what I had installed in the first place.
Now it probably is not completely like a fresh Ubuntu 16.04 install, as I suspect a few of the Ubuntu packages that were patched by the Elementary project still linger on. At some time in the future I might dive in and weed these out. The responsible thing would be to do this sooner rather than later, since by disabling the repositories these packages came from I also blocked off the route to security updates on them. But that might be the subject of a future blogpost.
Running Firefox in a 16.04 Libertine Container
The latest Ubuntu Touch image comes with the possibility of creating a Libertine container in which to install and run 'legacy' X11 apps. This feature is not new, since the last image of the mobile OS released by Canonical also had this functionality. What is new however is that with the upgrade to 16.04 the containers that are created are also based on an Ubuntu 16.04 chroot.
In the previous post I detailed how to install command-line utilities in such a container. In this post I will focus on installing a graphical application, namely Firefox.
Once the container is created, (for instructions on how to do that, see the previous post) it should be trivial to install firefox:
It turns out that there is an unspecified bug that causes all versions of Firefox newer than at least 45 to crash on certain architectures. To date, crashes on i386 and armhf have been reborted. Luckily there is a version 45 of Firefox still available in de Ubuntu repositories for 16.04. So we can try that one. First we remove the current firefox:
However, in the specific case of Firefox, there is an in app setting that will increase the rendering size of the UI. In the address bar enter: about:config. You might get a warning page about voiding your warranty. Click on "I accept the risk!" and proceed. In the search bar at the top of the resulting page type: devPix. You should now see the configuration setting: layout.css.devPixelsPerPx. Edit the value to something between 1.5 and 2. I have it set to 1.75 on my tablet. This give a nice increase in size, without taking up too much extra space and causing items inside pages to overlap.
Now that the controls are big enough for us to be able to tap on them, we need to tackle the annoying behavior that causes every menu or popup screen to open in its own window. Actually, it is more than just annoying, it makes the applications unusable. Good thing this is Linux, so all that is needed is to tweak a config text file somewhere.
The information to do this came from this post on the UBports forum. But I will recapitulate the instructions below.
First off, make the root filesystem writeable:
Lastly, since we installed an older version of the Firefox package, if and when we update all the packages from the container, Firefox will also be updated to the latest version. To stop this from happening we need to tell the package manager that we want to pin Firefox to the version we have installed. First we need to gain root access to our container. This is achieved with:
If we should tire of Firefox, or we wnat to delete it to reclaim storage space on the device we can do:
To install any of these deb files do the following:
In the previous post I detailed how to install command-line utilities in such a container. In this post I will focus on installing a graphical application, namely Firefox.
Update:
@TartanSpartan on Telegram has brought to my attention a github repo that contains recent builds of Firefox (65 at the time of this writing) for armhf achitecture that have the mentioned bugs patched. The releases can be found at https://github.com/jdonald/firefox-armhf/releases. Scroll down for the installation instructions.Update 2:
Since version 69 the bugs that caused Firefox to crash have been resolved. The package of the latest version available in the repos can be intsalled instead of following the steps in this post.Installation
One of the first graphical applications many (including me) want to install in a container is the Firefox browser. I mean, imagine having the power of a fully featured browser, including any extensions or plugins that would run on ARM, on your mobile device. Do I hear echos of convergence?Once the container is created, (for instructions on how to do that, see the previous post) it should be trivial to install firefox:
$ libertine-container-manager install-package -i xenial -p firefoxLet it finish installing, head over to the Libertine scope and tap on the Firefox icon... And it crashes... 😞
It turns out that there is an unspecified bug that causes all versions of Firefox newer than at least 45 to crash on certain architectures. To date, crashes on i386 and armhf have been reborted. Luckily there is a version 45 of Firefox still available in de Ubuntu repositories for 16.04. So we can try that one. First we remove the current firefox:
$ libertine-container-manager remove-package -i xenial -p firefoxthen we install the version we want:
$ libertine-container-manager install-package -i xenial \ -p firefox=45.0.2+build1-0ubuntu1Once the installation finishes we can try again, and this time Firefox does launch. There are still a few issues to tackle to enhance the user experience though.
Configuration
Because the dpi of the devices is high and the screens are small, the text and icons are minuscule. This is an issue with most X11 applications running in a libertine container, and there are workarounds, for the text at least, but none of them are ideal, and I will not reproduce them here.However, in the specific case of Firefox, there is an in app setting that will increase the rendering size of the UI. In the address bar enter: about:config. You might get a warning page about voiding your warranty. Click on "I accept the risk!" and proceed. In the search bar at the top of the resulting page type: devPix. You should now see the configuration setting: layout.css.devPixelsPerPx. Edit the value to something between 1.5 and 2. I have it set to 1.75 on my tablet. This give a nice increase in size, without taking up too much extra space and causing items inside pages to overlap.
Now that the controls are big enough for us to be able to tap on them, we need to tackle the annoying behavior that causes every menu or popup screen to open in its own window. Actually, it is more than just annoying, it makes the applications unusable. Good thing this is Linux, so all that is needed is to tweak a config text file somewhere.
The information to do this came from this post on the UBports forum. But I will recapitulate the instructions below.
First off, make the root filesystem writeable:
$ sudo mount -o remount,rw /then edit the file at
/usr/bin/libertine-xmir using sudo by changing the lineXmir -rootless $@to
Xmir -rootless -flatten $@exit and save the file. Remember to remount the filesystem read-only returning things to the way we found them:
$ sudo mount -o remount,ro /
Lastly, since we installed an older version of the Firefox package, if and when we update all the packages from the container, Firefox will also be updated to the latest version. To stop this from happening we need to tell the package manager that we want to pin Firefox to the version we have installed. First we need to gain root access to our container. This is achieved with:
$ libertine-container-manager exec -i xenial -c /bin/bashSome errors will be printed, but these can safely be ignored, and we will be landed in a root shell in the container. Once there type:
# apt-mark hold firefoxand our Firefox package will not be updated. It will not even be able to be removed!
If we should tire of Firefox, or we wnat to delete it to reclaim storage space on the device we can do:
# apt-mark unhold firefoxthen exit the container shell. The package can now be removed.
Caveat emptor
Running Firefox on a touch device does not automagically convert it into a touch aware application. Especially scrolling provides a very poor user experience. It should also not be forgotten that we are running a very old version of Firefox in our Libertine container. This could be a security risk, but it is a risk I am willing to accept. I intend to use Firefox for the few websites that refuse to play well with the native browser on the device. Also if the container should be compromised in any way, I could easily delete it and start again with a fresh one, sans any loss of data on the device.Installing newer versions of Firefox
@TartanSpartan on Telegram brought to my attention a repo containing recent builds of Firefox that do run on armhf. I have had inconsistent results with these builds, so YMMV.To install any of these deb files do the following:
- Navigate to https://github.com/jdonald/firefox-armhf/releases on your UTouch device.
- Download the version of your choice. Just make sure it is compiled to run on 16.04. I clicked on firefox_65.0+build2-0ubuntu0.16.04.1_armhf.deb as that was the lastest build at the time of this writing.
- Navigate to the Downloads folder in the File Manager app and copy the name of the downloaded file to the clipboard. You really don't want to be typing it out in the next step.
- Next go to the Libertine Manager in the Systems Settings app.
Click on the container you would like to install Firefox in and then click on the + icon in the upper right corner.
Select Enter package name of Debian file. In the edit box type the complete path to the downloaded deb file. In my case that was /home/phablet/Downloads/firefox_65.0+build2-0ubuntu0.16.04.1_armhf.deb. Hit enter or click on OK and the package, including any dependencies, will be installed.
Labels:
firefox,
libertine,
ubports,
ubuntu,
ubuntu
touch
Monday, September 10, 2018
Running additional command line tools on Ubuntu Touch
On April 5th, 2017 Mark Shuttleworth founder of the Ubuntu project and of Canonical, the company that sponsors the project, dropped, what many in the Ubuntu community would consider, a bombshell. He announced that the company would be ending their investment in Unity8, the phone and development of a convergent experience for the user across multiple devices and form factors
The news left me reeling. I felt left out in the cold, not to say betrayed, by Canonical. I had wholeheartedly embraced the vision Mark had pitched. And when the first Ubuntu Phone came out, severely underspecc'd and under-powered (even then) I bought it, partly to support the effort, partly to experience the journey first hand. I did the same when the first (and only) tablet came out. To me the fledgling mobile OS was much better suited as a tablet OS than a phone OS, as I didn't use WhatsApp on tablets, so I didn't miss it on one either.
But the very next day Marius Gripsgård, founder of the UBports project, posted a message to his G+ page that the UBports team would continue development of Ubuntu Touch, and Unity 8. I think I became aware of this initiative a few days later, and even then I had more of a wait and see attitude.
Fast forward to today and Ubuntu Touch is very much alive. A community has formed around the project, the likes of which Canonical had envisioned, but never managed to garner. The UBports team have released four OTA's since April 2017, the last of which, OTA-4, was released on August 26, 2018. This is an important milestone for the project, because it brings the base of the OS from 15.04 to 16.04, which will be supported till April 2021, and frees up the team to focus on features instead of having to backport security patches and work around ancient versions of libraries and other software components.
Needless to say, all my original devices are running Ubuntu Touch powered by UBports, and I even managed to source a Meizu Pro 5 from amazon.it, as that was a device that would eventually support Anbox (or at least it was, back then ...). I am currently running the release candidate of 16.04 on my BQ Aquaris M10 FHD tablet. And part of the charm of running a regular(-ish) Linux OS on the tablet is that I can open a terminal and poke around at stuff, and even do most of the things I would do on a laptop or a desktop computer.
One main difference between a regular PC install and the device image is that the root filesystem on the device is read-only. This is means that additional packages cannot be installed from the repositories out of the box. Of course this being Linux, you could remount the root file system as writable and sudo apt install to your hearts content, but there are drawbacks to that path.
So what could I do if I wanted additional command-line tools available on my tablet, like htop, nmap and screenfetch? The answer, as in so many other instances these days, would be: containers! No, I am not talking Docker or LXD here, but Libertine containers. This is the technology that makes it possible to install desktop applications like Firefox and LibreOffice on your Ubuntu Touch device. It does not magically make them usable on a 4.5" to 10" high dpi screen, though.
Starting with 16.04 there is a fancy section in the system settings where you can create and administer Libertine containers. But I will focus on how to do it from the command line because that is where I have had the most consistent success.
First you create your container. I am calling mine Xerus and giving it the id xenial:
To invoke the tools use libertine-launch. I will illustrate with screenfetch:
However, typing libertine-launch -i xenial <program name> every time I want to run one of the tools gets very tedious very quickly. But this being essentially a fully capable Linux OS running on a mobile device, a trick from the desktop transfers seamlessly to the device. Just edit (or create) the .bash_aliases file in the $HOME folder
Having a fully functional terminal in the palm of my hand never ceases to amaze me. And with this neat trick I can extend the toolset available to me and tailor it to my specific needs.
The news left me reeling. I felt left out in the cold, not to say betrayed, by Canonical. I had wholeheartedly embraced the vision Mark had pitched. And when the first Ubuntu Phone came out, severely underspecc'd and under-powered (even then) I bought it, partly to support the effort, partly to experience the journey first hand. I did the same when the first (and only) tablet came out. To me the fledgling mobile OS was much better suited as a tablet OS than a phone OS, as I didn't use WhatsApp on tablets, so I didn't miss it on one either.
But the very next day Marius Gripsgård, founder of the UBports project, posted a message to his G+ page that the UBports team would continue development of Ubuntu Touch, and Unity 8. I think I became aware of this initiative a few days later, and even then I had more of a wait and see attitude.
Fast forward to today and Ubuntu Touch is very much alive. A community has formed around the project, the likes of which Canonical had envisioned, but never managed to garner. The UBports team have released four OTA's since April 2017, the last of which, OTA-4, was released on August 26, 2018. This is an important milestone for the project, because it brings the base of the OS from 15.04 to 16.04, which will be supported till April 2021, and frees up the team to focus on features instead of having to backport security patches and work around ancient versions of libraries and other software components.
Needless to say, all my original devices are running Ubuntu Touch powered by UBports, and I even managed to source a Meizu Pro 5 from amazon.it, as that was a device that would eventually support Anbox (or at least it was, back then ...). I am currently running the release candidate of 16.04 on my BQ Aquaris M10 FHD tablet. And part of the charm of running a regular(-ish) Linux OS on the tablet is that I can open a terminal and poke around at stuff, and even do most of the things I would do on a laptop or a desktop computer.
One main difference between a regular PC install and the device image is that the root filesystem on the device is read-only. This is means that additional packages cannot be installed from the repositories out of the box. Of course this being Linux, you could remount the root file system as writable and sudo apt install to your hearts content, but there are drawbacks to that path.
- Firstly it would put your device in a state that is undefined, and that could cause the regular update mechanism to fail the next time an update of the system image is made available for the device. I have personally never seen the mechanism fail even after modifying the root system, but it is something to be aware of.
- Secondly, in case the system does update correctly, which it always has for me, then any packages you installed would have to be reinstalled after applying the update. As far as I understand the process, the system's root image is overwritten by the update, undoing any changes applied by the user.
- Lastly, and this is what led me to search for alternatives, the current system image for the M10 hardly has any free space for installing additional packages in the first place.
So what could I do if I wanted additional command-line tools available on my tablet, like htop, nmap and screenfetch? The answer, as in so many other instances these days, would be: containers! No, I am not talking Docker or LXD here, but Libertine containers. This is the technology that makes it possible to install desktop applications like Firefox and LibreOffice on your Ubuntu Touch device. It does not magically make them usable on a 4.5" to 10" high dpi screen, though.
Starting with 16.04 there is a fancy section in the system settings where you can create and administer Libertine containers. But I will focus on how to do it from the command line because that is where I have had the most consistent success.
First you create your container. I am calling mine Xerus and giving it the id xenial:
$ libertine-container-manager create-container -i xenial -n "Xerus"This might take a while to complete. Next install the command line tools we want to use in the newly created container.
$ libertine-container-manager install-package -i xenial -p htop $ libertine-container-manager install-package -i xenial -p nmap $ libertine-container-manager install-package -i xenial -p screenfetch
To invoke the tools use libertine-launch. I will illustrate with screenfetch:
$ libertine-launch -i xenial screenfetch
: DISPLAY environment variable not set!
[[ ! ]] awk: fatal: cannot open file `/sys/devices/system/cpu/cpu0/
cpufreq/scaling_max_freq' for reading (Permission denied)
./+o+- phablet@android
yyyyy- -yyyyyy+ OS: Ubuntu 16.04 xenial
://+//////-yyyyyyo Kernel: aarch64 Linux 3.10.93+
.++ .:/++++++/-.+sss/` Uptime: 2m
.:++o: /++++++++/:--:/- Packages: 679
o:+o+:++.`..```.-/oo+++++/ Shell: 21829
.:+o:+o/. `+sssoo+/ CPU: MT8163
.++/+:+oo+o:` /sssooo. RAM: 1324MiB / 1962MiB
/+++//+:`oo+o /::--:.
\+/+o+++`o++o ++////.
.++.o+++oo+:` /dddhhh.
.+.o+oo:. `oddhhhh+
\+.++o+o``-````.:ohdhhhhh+
`:o+++ `ohhhhhhhhyo++os:
.o:`.syhhhhhhh/.oo++o`
/osyyyyyyo++ooo+++/
````` +oo+++o\:
`oo++.
OK, so it's not perfect, as every command you run in this way will always give that : DISPLAY environment variable not set!
warning. But this a command line tool, so that doesn't bother me. The fatal error in awk is more serious. It only happens with the screenfetch command, but that undoubtedly has to do with the command running from inside a container, so I ignore that as well.However, typing libertine-launch -i xenial <program name> every time I want to run one of the tools gets very tedious very quickly. But this being essentially a fully capable Linux OS running on a mobile device, a trick from the desktop transfers seamlessly to the device. Just edit (or create) the .bash_aliases file in the $HOME folder
$ nano .bash_aliasesAnd add the following lines
alias htop='libertine-launch -i xenial htop' alias nmap='libertine-launch -i xenial nmap' alias screenfetch='libertine-launch -i xenial screenfetch'Log out, log in and then you can use the short form like so:
$ htop
Having a fully functional terminal in the palm of my hand never ceases to amaze me. And with this neat trick I can extend the toolset available to me and tailor it to my specific needs.
Monday, May 21, 2018
Setting up an encrypted /home partition with LVM and LUKS
My shiny new Slimbook Katana II laptop recently arrived. And I am very pleased with its looks. I got the black model.
 Mine is fitted with an Intel i7 8th gen processor, 16 GB of RAM, a 120 GB SSD and a secondary HD of 1 TB.
Mine is fitted with an Intel i7 8th gen processor, 16 GB of RAM, a 120 GB SSD and a secondary HD of 1 TB.
Lots of room to play around with VM's, LXD containers and Docker containers. I also particularly like that it comes with a penguin on the SUPER key, instead of a Windows logo. It also has a badge that says: "Powered by GNU/Linux".
This being a laptop and us living in this day and age, I decided I wanted two things. I wanted the OS to have one logical pool of storage to draw from and I wanted the /home partition to be encrypted. The first requirement can be met with LVM, the second with LUKS. But I had never used the two combined.
Setting up LVM at install time for Ubuntu is quite straight forward. It is one of the options in the setup wizard. Unfortunately the wizard does not provide any obvious way to customize the LVM setup in
a similar way that the Anaconda installer does on Red Hat based distros. Ubiquity only lets you choose which hard disk you want to install the LVM on. I chose the SSD.
At the end of the installation the LVM situation looks as follows:
But what about my 1TB disk? Well, I will need to make LVM aware of it myself. Here I will go into some more detail as to how I want the final system to be configured. I want to dedicate 500 GB of disk space to the var logical volume as that is where all the data for the virtual machines and containers will reside. I also thought I would start out with 100GB of space for my home logical volume. Notice that this would not use all of the 1 TB of space I have available. I am using LVM, so I figure I can always resize the logical volume if I need more space. (That should be possible to do, even if the file system on the home logical volume will be encrypted. But I will cross that bridge when I reach it. If it gives me trouble, that will be the subject of another blog post.) I will mostly just jot down the commands that I used without explaining them in depth. Your preferred search engine and the man pages for the fine grained usage details of each command.
Let's get to it then. My SSD was assigned to /dev/sda. I had assigned some space at the beginning for a recovery partition of sorts.
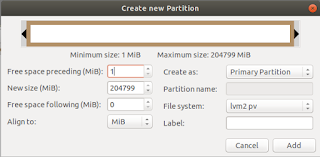 I still need to decide how I want that to work exactly. But the rest of the 1 TB of space I want to add to the ubuntu-vg volume group. So first I booted the 18.04 installation media and elected to enter the live session. There I fired up gparted (because I like me a graphical user interface if I can use one) and created a partition filling the rest of the disk and assigned it the file system lvm2 pv.
I still need to decide how I want that to work exactly. But the rest of the 1 TB of space I want to add to the ubuntu-vg volume group. So first I booted the 18.04 installation media and elected to enter the live session. There I fired up gparted (because I like me a graphical user interface if I can use one) and created a partition filling the rest of the disk and assigned it the file system lvm2 pv.
Now the physical volume situation looks as follows:
Now that the encryption is in place, we have to unlock the volume to be able to format it and copy over the contents of /home to it.
What have we achieved thus far?
First we will notify the kernel of the encrypted volume. We do this by editing /etc/crypttab and adding the following encry:
 Mine is fitted with an Intel i7 8th gen processor, 16 GB of RAM, a 120 GB SSD and a secondary HD of 1 TB.
Mine is fitted with an Intel i7 8th gen processor, 16 GB of RAM, a 120 GB SSD and a secondary HD of 1 TB.Lots of room to play around with VM's, LXD containers and Docker containers. I also particularly like that it comes with a penguin on the SUPER key, instead of a Windows logo. It also has a badge that says: "Powered by GNU/Linux".
This being a laptop and us living in this day and age, I decided I wanted two things. I wanted the OS to have one logical pool of storage to draw from and I wanted the /home partition to be encrypted. The first requirement can be met with LVM, the second with LUKS. But I had never used the two combined.
Setting up LVM at install time for Ubuntu is quite straight forward. It is one of the options in the setup wizard. Unfortunately the wizard does not provide any obvious way to customize the LVM setup in
a similar way that the Anaconda installer does on Red Hat based distros. Ubiquity only lets you choose which hard disk you want to install the LVM on. I chose the SSD.
At the end of the installation the LVM situation looks as follows:
root@ubuntu:~# pvs PV VG Fmt Attr PSize PFree /dev/sdb1 ubuntu-vg lvm2 a-- <120,00g 44,00m root@ubuntu:~# lvs LV VG Attr LSize ... root ubuntu-vg -wi-ao---- 119,00g swap_1 ubuntu-vg -wi-ao---- 976,00m root@ubuntu:~#The installer allocated one physical volume, /dev/sdb1, to LVM, and assigned it to the ubuntu-vg volume group. Within that volume group it created two logical volumes, named root and swap_1. The root file system / is mounted under root and swap space is mounted under swap_1.
But what about my 1TB disk? Well, I will need to make LVM aware of it myself. Here I will go into some more detail as to how I want the final system to be configured. I want to dedicate 500 GB of disk space to the var logical volume as that is where all the data for the virtual machines and containers will reside. I also thought I would start out with 100GB of space for my home logical volume. Notice that this would not use all of the 1 TB of space I have available. I am using LVM, so I figure I can always resize the logical volume if I need more space. (That should be possible to do, even if the file system on the home logical volume will be encrypted. But I will cross that bridge when I reach it. If it gives me trouble, that will be the subject of another blog post.) I will mostly just jot down the commands that I used without explaining them in depth. Your preferred search engine and the man pages for the fine grained usage details of each command.
Let's get to it then. My SSD was assigned to /dev/sda. I had assigned some space at the beginning for a recovery partition of sorts.
 I still need to decide how I want that to work exactly. But the rest of the 1 TB of space I want to add to the ubuntu-vg volume group. So first I booted the 18.04 installation media and elected to enter the live session. There I fired up gparted (because I like me a graphical user interface if I can use one) and created a partition filling the rest of the disk and assigned it the file system lvm2 pv.
I still need to decide how I want that to work exactly. But the rest of the 1 TB of space I want to add to the ubuntu-vg volume group. So first I booted the 18.04 installation media and elected to enter the live session. There I fired up gparted (because I like me a graphical user interface if I can use one) and created a partition filling the rest of the disk and assigned it the file system lvm2 pv.Now the physical volume situation looks as follows:
root@ubuntu:~# pvs PV VG Fmt Attr PSize PFree /dev/sda2 lvm2 a-- <916,61g <315,61g /dev/sdb1 ubuntu-vg lvm2 a-- <120,00g 44,00m root@ubuntu:~#Notice that, while LVM is aware of the new physical volume, it has not been assigned to any volume group (VG) as yet. Let's remedy that:
root@ubuntu:~# vgextend ubuntu-vg /dev/sda2 Volume group "ubuntu-vg" successfully extended root@ubuntu:~# pvs PV VG Fmt Attr PSize PFree /dev/sda2 ubuntu-vg lvm2 a-- <916,61g <315,61g /dev/sdb1 ubuntu-vg lvm2 a-- <120,00g 44,00m root@ubuntu:~#That's better. Now we create our two logical volumes. First we'll tackle var since that just needs to be created and formatted:
root@ubuntu:~# lvcreate -L 500G -n var ubuntu-vg Logical volume "var" created root@ubuntu:~# mkfs -t ext4 /dev/ubuntu-vg/var # Output of this command omitted for brevity root@ubuntu:~#The making of the home volume group is just slightly more involved, since I want to have encrypted additionally:
root@ubuntu:~# lvcreate -L 100G -n home ubuntu-vg Logical volume "home" created root@ubuntu:~#Now we will encrypt the volume. First we scramble the contents:
root@ubuntu:~# shred --verbose --random-source=/dev/urandom \ --iterations=3 /dev/ubuntu-vg/home ...By performing this operation we fill the whole partition with random bytes, making it impossible for a snooper to see what parts of the volume contain data and what parts dont. But be patient. This might take a while to complete. Next we setup the encryption:
root@ubuntu:~# cryptsetup --verbose --cipher aes-xts-plain64 \ --key-size 512 --hash sha512 --iter-time 5000 \ --use-random luksFormat /dev/ubuntu-vg/home WARNING! ======== This will overwrite data on /dev/ubunut-vg/home irrevocably. Are you sure? (Type uppercase yes): YES Enter LUKS passphrase: Verify passphrase: Command successful. root@ubuntu:~#Be sure to remember the passphrase you entered here. Write it down on a slip of paper and store that in a safe. Or use a password manager. But do not loose it!! You will be in a world of pain if you do.
Now that the encryption is in place, we have to unlock the volume to be able to format it and copy over the contents of /home to it.
root@ubuntu:~# cryptsetup open --type luks \ /dev/ubuntu-vg/home encrypted_home Enter passphrase for /dev/ubuntu-vg/home: root@ubuntu:~# mkfs -t ext4 /dev/mapper/encrypted_home ...Right... Almost there. Now we make temporary mount points for the root, var and home volume groups to populate the latter two with the contents from the former. Remember that we are doing all of this from a live session:
root@ubuntu:~# mkdir /mnt/{root,var,home}
root@ubuntu:~# mount /dev/ubuntu-vg/root /mnt/root
root@ubuntu:~# mount /dev/ubuntu-vg/var /mnt/var
root@ubuntu:~# mount /dev/mapper/encrypted_home /mnt/home
root@ubuntu:~# rsync -avz /mnt/root/var/ /mnt/var
...
root@ubuntu:~# rsync -avz /mnt/root/home/ /mnt/home
...
root@ubuntu:~# umount /mnt/{root,var,home}
root@ubuntu:~# cryptsetup close encrypted_home
Notice that I did not clean up the old home and var directories under /mnt/root. As this was a clean install they don't take up so much space. And leaving them put guarantees I have a bootable system if for whatever reason the logical volumes cannot be mounted.What have we achieved thus far?
- We've extended the volume group to encompass both disks.
- We've added var and home logical volumes to house our /var and /home partitions.
- We've setup LUKS encryption for the home logical volume.
- We've copied the contents from the old /home and /var directories to the designated logical volumes.
First we will notify the kernel of the encrypted volume. We do this by editing /etc/crypttab and adding the following encry:
root@ubuntu:~# nano /etc/crypttab
encrypted_home /dev/mapper/ubuntu--vg-home none luks,discardAnd finally we edit /etc/fstab and add our new mount points:
root@ubuntu:~# nano /etc/fstab
/dev/mapper/ubuntu--vg-var /var ext4 errors=remount-ro 0 1 /dev/mapper/encrypted_home /home ext4 errors=remount-ro 0 1The complete file looks like this on my system:
# /etc/fstab: static file system information. # # Use 'blkid' to print the universally unique identifier for a # device; this may be used with UUID= as a more robust way to name # devices that works even if disks are added and removed. See fstab(5). # #And we're done! Reboot your machine and see if it all works as it should. Mine didn't but that was because I misspelt the name of the /etc/crypttab file. After I corrected the typo all went as it should./dev/mapper/ubuntu--vg-root / ext4 errors=remount-ro 0 1 /dev/mapper/ubuntu--vg-swap_1 none swap sw 0 0 /dev/mapper/ubuntu--vg-var /var ext4 errors=remount-ro 0 1 /dev/mapper/encrypted_home /home ext4 errors=remount-ro 0 1
Thursday, March 22, 2018
Where have all the comments gone?
I changed the domain of the blog, from arubislander.blogspot.com to blog.arubislander.nl There was a warning that changing the domain would "adversely affect" the existing comments. So I had been warned ...
Wednesday, March 21, 2018
Rebooting the Blog
It has been five months since the last post to this blog. In the intervening time, I got to thinking what I wanted to do with this space. So I decided to switch focus.
Originally I had intended this blog to document the "journeys of the Starship Enterprise", or at least my journey of discovery in the realm of software development. But I have to face the fact that, either I don't do much discovering I think worth blogging about, or I am very very bad at documenting my discoveries. On the other hand, there have been things I have come accross that have been helpful at the time. But when I want to go back and review them, or re-apply them or dig deeper, I would have trouble finding the resource again.
Because of the above I am going to reboot this blog by repurposing it. The primary audience for it will be myself, future me to be exact. This will be the place where I jot down stuff I find and want to be able to return to for reference.
If someone else also derives some benefit of it, all the better!
Originally I had intended this blog to document the "journeys of the Starship Enterprise", or at least my journey of discovery in the realm of software development. But I have to face the fact that, either I don't do much discovering I think worth blogging about, or I am very very bad at documenting my discoveries. On the other hand, there have been things I have come accross that have been helpful at the time. But when I want to go back and review them, or re-apply them or dig deeper, I would have trouble finding the resource again.
Because of the above I am going to reboot this blog by repurposing it. The primary audience for it will be myself, future me to be exact. This will be the place where I jot down stuff I find and want to be able to return to for reference.
If someone else also derives some benefit of it, all the better!
Subscribe to:
Posts (Atom)

